Security
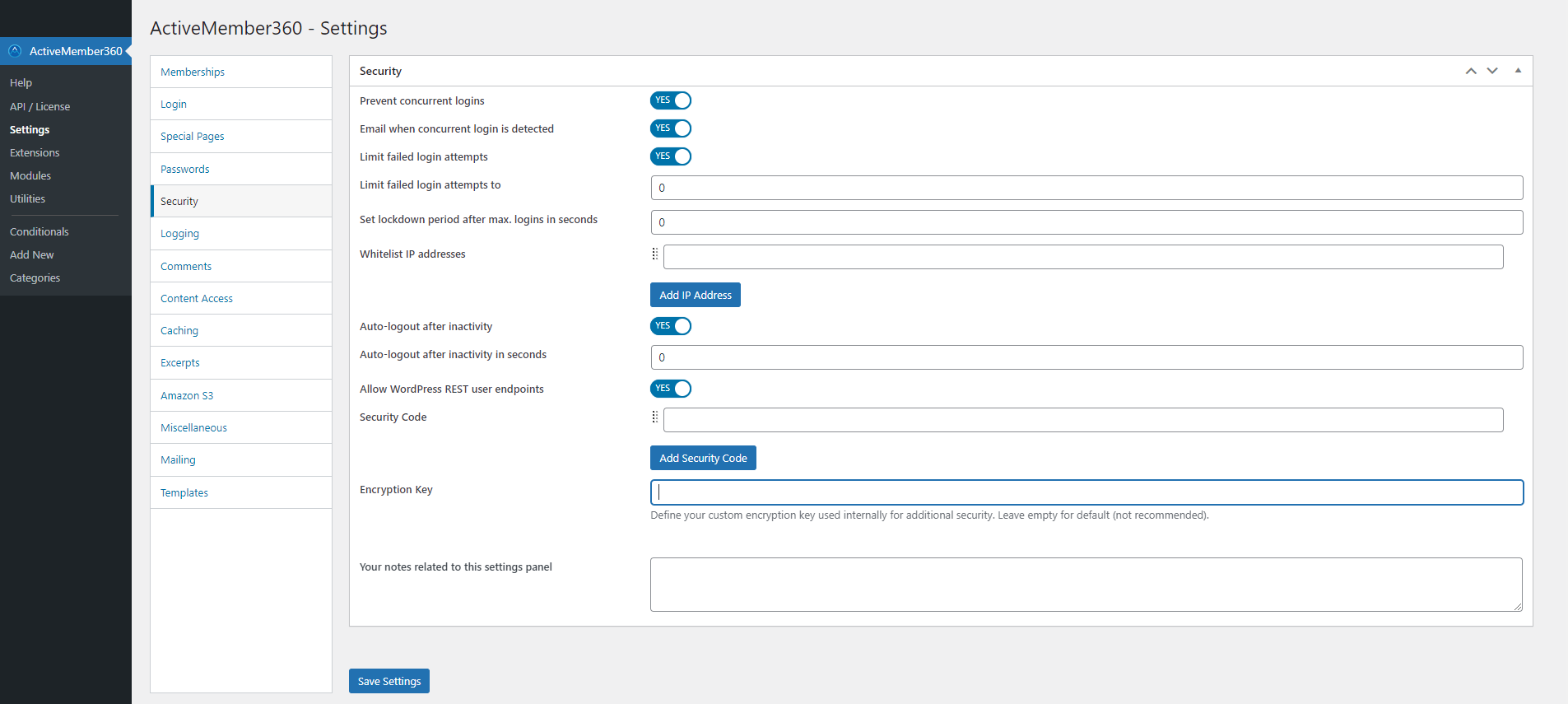
Prevent concurrent logins
When Prevent concurrent login is set to Yes/On concurrent logins from users with the same login credentials are prevented.
When a concurrent login occurs the user who is currently logging in is authenticated and allowed access to the site.
However any other WordPress sessions currently active for that user will be terminated i.e. the user is effectively logged out.
A message is shown in the browser for all sessions that have been terminated by concurrent login.
A concurrent login can occur if the user logs in from a different browser window, and/or different device. It is not dependent upon IP address.
Default: No
Email when concurrent login is detected
This option is only shown and the setting applied if ActiveMember360, Settings, Security, Prevent concurrent logins is set to Yes.
Set Email when concurrent login is detected to Yes/On to send an email when a concurrent login is detected.
The email will be sent to the email address as defined in ActiveMember360, Settings, Mailing, Default "Mail From" address.
The notification email is automatically scheduled to send every hour. After the first email further emails will only contain details of concurrent logins since the last notification email was sent.
The details contained within the email includes for each concurrent login:
- WordPress User ID
- WordPress Username or Email Address
- WordPress First Name
- WordPress Last Name
- Date and time of concurrent login using server time
If Email when concurrent login is detected is set to No/Off concurrent login information will be available from within the WordPress database. It is stored within the WordPress options table in the record with the option_name site_concurrent_logins
Default: No
Limit failed login attempts
When Limit failed login attempts is set to Yes/On any visitor will be blocked after a certain amount of failed login attempts.
The number of failed login attempts allowed before being blocked are set in ActiveMember360, Settings, Security, Limit failed login attempts to.
Once the number of failed login attempts have been reached the IP address used for the login attempts will be banned from access to your site until the specified ActiveMember360, Settings, Security, Set lockdown period after max. logins in seconds has expired.
Default: No
Limit failed login attempts to
This option is only shown and the setting applied if ActiveMember360, Settings, Security, Limit failed login attempts is set to Yes.
Set Limit failed login attempts to as the consecutive number of failed login attempts by any visitor after which they will be blocked from the site.
Default: 0 i.e same as Limit failed login attempts being set to No/Off
Set lockdown period after max. logins in seconds
This option is only shown and the setting applied if ActiveMember360, Settings, Security, Limit failed login attempts is set to Yes.
Specify for Set lockdown period after max. logins in seconds as the number of seconds for which a visitor will be blocked from the site after hitting the consecutive number of failed login attempts as set in Limit failed login attempts to.
Default: 0
Whitelist IP addresses
This option is only shown and the setting applied if ActiveMember360, Settings, Security, Limit failed login attempts is set to Yes.
List any IP addresses, which will be ignored by the ActiveMember360, Settings, Security, Limit failed login attempts feature.
Default: None
Auto-logout after inactivity
Set for Auto-logout after inactivity a time interval to automatically logout a user if they are inactive on the site.
Each time a new page is viewed, the timer is reset.
A setting of 0 will disable it.
Default: 0
Auto-logout after inactivity in seconds
This option is only shown and the setting applied if ActiveMember360, Settings, Security, Auto-logout after inactivity is set to Yes.
Set for Auto-logout after inactivity a time interval to automatically logout a user if they are inactive on the site.
Each time a new page is viewed, the timer is reset.
A setting of 0 will disable it.
Default: 0
Allow WordPress REST user endpoints
Set Allow WordPress REST user endpoints to Yes/On to allow access to WordPress REST user endpoints.
For security reasons this should typically be set to No/Off. However if the WordPress REST user endpoints are required by WordPress, or other third party plugins or applications integrated with your WordPress site, it should be set to Yes/On.
For example the WordPress Block Editor uses the REST user endpoints to allow an author to be chosen when creating/editing a page/post. If that functionality is required set Allow WordPress REST user endpoints to Yes/On at least temporarily.
Default: Yes
Security Codes
Define as many Security Codes as required.
These are used with ActiveMember360 Webhook Modules and the ActiveMember360, Modules, Autologin for authentication purposes.
We recommend that you use only the following alphanumerics and special characters. This will ensure that your codes are safe for use with all webhook URLs:
1234567890abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ$-_.~
Default: None
Encryption Key
Define your custom Encryption Key used internally for additional security.
It is highly recommended that you define your own key rather than use the default.